By The Cougar Chronicle Staff
SAN DIEGO — A local Internet security expert praised CSUSM’s detective work that brought down an election-rigging scheme on campus last spring. But the case against the ex-student charged with the crime shows how vulnerable computers — and their users — can be to cybercrime.
On Feb. 8, Matt Weaver was charged in federal court with two counts of wire fraud, one count of access device fraud and one count of unauthorized access to a computer, for allegedly attempting to rig the votes in the ASI election in March 2012. The criminal complaint said that Weaver, who was running for the office of ASI president, purchased and installed up to 15 keylogging devices on 19 on-campus computers in order to gather the username and passwords of 740 students (which he allegedly used to cast votes for himself).
Chris Gruenwald, owner of Bayside Networks in Sorrento Valley, described the ASI election-hacking scheme as “an aggressive, primitive act” that is likely to have severe consequences if Weaver is found guilty.
“He sounds like a young wise guy who thinks he’s the smartest guy in the room,” Gruenwald said, adding that if Weaver is found guilty of the crimes, then: “he’s ruined his life and thrown away a good chance at an education for something he didn’t really think through.”
Gruenwald described keylogger hacking as a relatively unsophisticated form of cybercrime.
“Installing these devices is like physically breaking into a house,” said Gruenwald, whose 26-year-old company provides information technology and troubleshooting support to small and mid-sized companies. “He didn’t do anything people would begin to consider clever.”
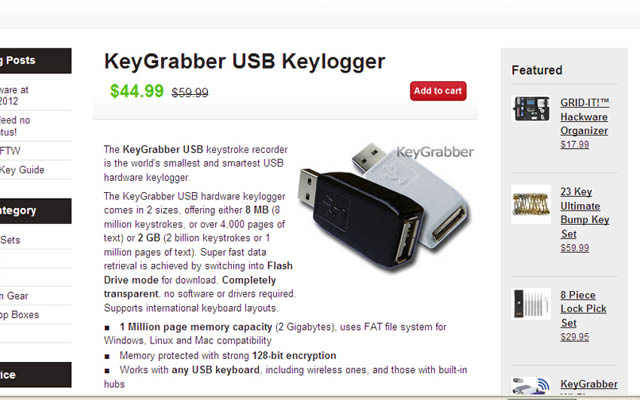
A keylogger is a simple, finger-sized device that can be plugged in between a computer’s keyboard cord and its CPU hard drive to log each keystroke. Investigators say they found evidence on Weaver’s laptop that he purchased several keyloggers in the months leading up to the election. They also found a record of Internet search queries on the laptop for phrases such as “invasion of privacy cases,” “jail time for keylogger” and “how to rig an election.”
Although keyloggers can be purchased online, Gruenwald said they’re not seen as a legitimate business product. “I can’t begin to think what kind of legitimate purpose there could be. It’s a hacking tool.”
Although university IITS staff did not detect the keyloggers on the computers during the two to three months they were being used to gather data, Gruenwald praised the IITS team for discovering Weaver’s alleged efforts to cast the illicit votes.
According to investigators, alert systems staff noticed clusters of votes coming in from the same campus IP addresses (an internet access points) on four separate occasions during election week. They were able to trace the final surge of 259 votes to a laptop that Weaver was using in Academic Hall 202 on the final day of voting, March 15. Network administrators remotely accessed his computer screen to watch what he was doing, and another staffer entered Academic Hall 202 and used a cell phone camera to film Weaver allegedly cutting and pasting students’ logins and passwords into the voting system.
“It’s interesting that the university was following some checklist of best practices for managing the voting system,” Gruenwald said. “That’s something that could’ve been overlooked very easily but they were paying attention and they need to be complimented on that.”
Margaret Lutz Chantung of the communications office said that details of the university’s methods of enforcing internet security are somewhat private. The keyloggers were removed from the on-campus computers and “the university now has methods and policies in place to detect keyloggers,” Lutz Chantung said.
Gruenwald said that the whole experience should shatter any illusion students have that the work they do on campus computers—or any centrally administered network system—is private.
“Universities always have students trying to get away with stuff, but everything is tracked,” he said. “You can bet that most any computer you don’t own, that’s managed in some central way, has a tool where they can hop on and see what a user’s doing. He thought he was the hacker, and he got hacked right back.”